New name, same mission, Fox Crypto becomes Sentyron. Learn more ->
Media and file encryption
When handling classified material, the use of laptops and USB poses significant security risks. These devices are vulnerable to cyber attacks, such as hacking or phishing, which can lead to sensitive information being exposed or stolen.
Additionally, physical theft or loss of a laptop or USB drive can result in the accidental dissemination of classified content, especially if proper encryption or access controls are not in place. Without stringent security measures, these common tools can become gateways for adversaries seeking to compromise national security or proprietary information.
Secured with hardware encryption solutions, our Hiddn solution offers powerful protection against unauthorized access to sensitive data – at the highest levels.
Protect your organization against advanced threats
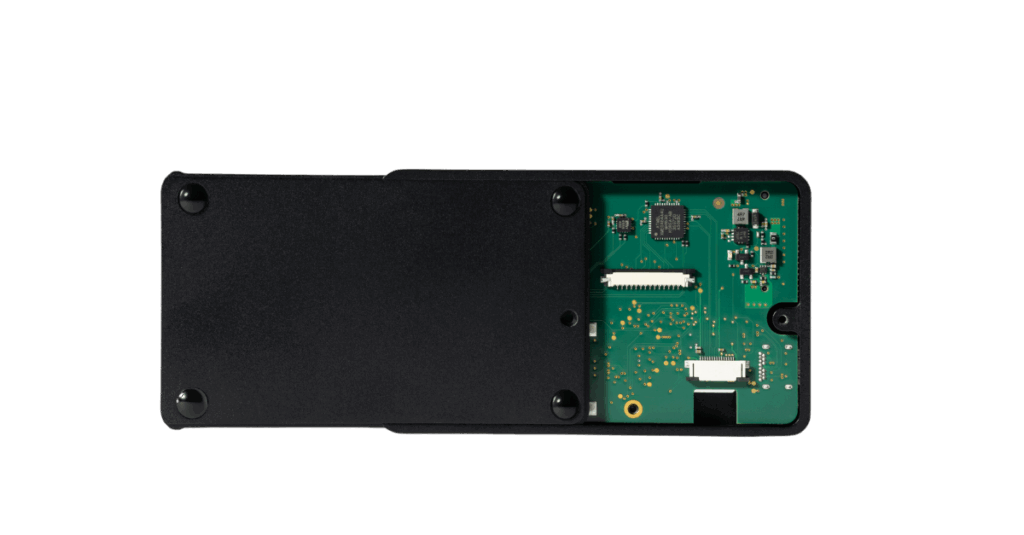
We offer two solutions: the SafeDisk for laptops and the CRYPTR for external storage. Both Hiddn SafeDisk and Hiddn CRYPTR use strong encryption and two-factor authentication. The solutions include a key management application for the encrypted disks.
The SafeDisk protects data-at-rest on your laptop. The SafeDisk consists of an integrated tamper-proof crypto module with full AES disk encryption, using 256-bit keys and two-factor authentication using a smart card and password. The keys are generated by the Hiddn Card Management System. As the encryption key is actively removed from the SafeDisk after use and stored on the tamper-proof smart card, the SafeDisk offers very high security value.
The Hiddn Card Management System is used to create the smart cards for access and configuration of the crypto modules, and is built with a PKI security architecture.
The CRYPTR can be used as an external hard drive or as a bootable external disk. The CRYPTR has an integrated tamper-proof crypto module with full AES disk encryption, which uses 256-bit keys and two-factor authentication by means of a smart card and PIN code. The keys are generated by the Hiddn Card Management System.
The solution is resistant to key-loggers and brute-force attacks.
Direct zeroization resets unit to factory default state.
Hiddn offers the perfect solution for transportation of data between the office and other places.
The solution requires both a PIN and a smart card.
The optional CMS enables an administrator to be in control of the keys, units, and users.
The CRYPTR solution has a bright, easy to read OLED display that informs the user about the status of the device.
The secure bootable CRYPTR makes it possible to use any computer and still operate in a secure environment.
The disks can be used straight out of the box, not requiring any software or drivers to be installed prior to use.

Government institutions handle vast amounts of sensitive and classified information daily, from policy decisions to citizen data. The security of this information is crucial to maintaining national stability and public trust.
However, these organizations are frequent targets of cyber threats, including espionage, data breaches, and digital manipulation.

SMEs such as IT service providers, contractors, and other organizations have to deal with strict security regulations. With NIS2, the need for properly securing your data has only increased.
The Hiddn solution allows organizations to decide on the size of their disks, offering a flexible solution for companies of all sizes.

Large international corporations have to protect sensitive data. Attackers are always looking for ways in to get ahold of this information.
Protect your secrets and your people by using the most secure data storage solution.

In the defence sector, safeguarding classified information is critical to national security. Military organizations are constantly exposed to cyber threats, including espionage, data manipulation, and cyber warfare. Ensuring the secure exchange of sensitive information is essential to protecting military operations from both current and emerging threats.

Over twenty years of experience
As a pioneer in high-assurance security solutions, Sentyron brings more than twenty years experience in protecting classified information and data.